
Scroll
NIST
Let our security experts discover your vulnerabilities before cybercriminals do.
What is NIST CSF?
The NIST cybersecurity framework is a tool for organisations to improve their cybersecurity posture through the provision of sets of guidelines and The NIST cybersecurity framework is a tool that provides sets of guidelines and best practices to help organisations build and improve their cybersecurity posture. This will allow the organisations to be fully prepared for identifying and detecting cyber-attacks as well as responding, preventing and recovering from cyber incidents. The framework categorises all cybersecurity capabilities, projects, processes and daily activities into 5 core functions:
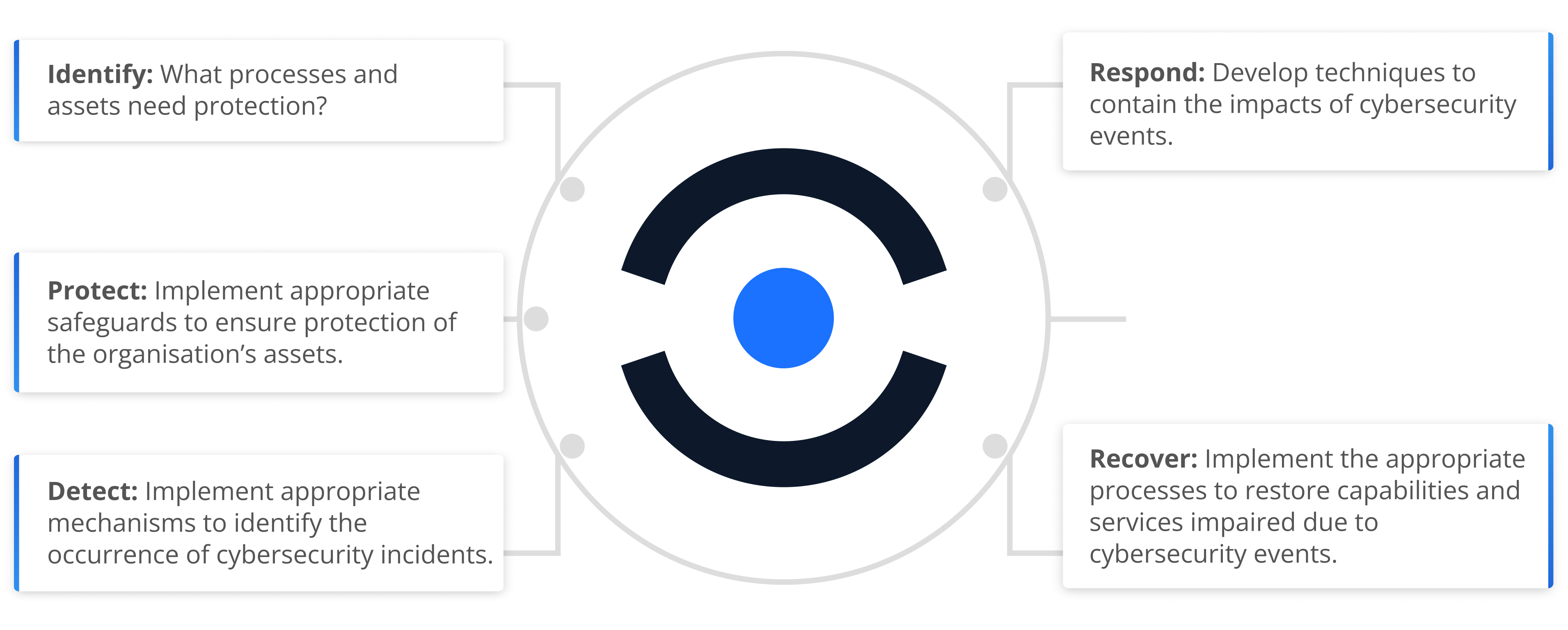
Identify: What processes and assets need protection?
Protect: Implement appropriate safeguards to ensure protection of the organisation’s assets.
Detect: Implement appropriate mechanisms to identify the occurrence of cybersecurity incidents.
Respond: Develop techniques to contain the impacts of cybersecurity events.
Recover: Implement the appropriate processes to restore capabilities and services impaired due to cybersecurity events.

How We Work:
Our approach is designed to enhance your organisation’s security posture. Our consultants follow a structured process that includes assessing your current state, establishing a strategy and finally, implementation. The steps included are:
Assessing:
In this initial phase, our consultants will conduct an assessment of your cyber security status and any potential risks, involving:
- An exercise to identify and document your critical assets and data flows.
- A gap analysis against the NIST Cybersecurity Framework.
- Engagement with key stakeholders.
- Vulnerability assessments assessments and threat modelling.
Strategising:
Based on our assessment findings, we will develop a tailored strategy specific to you:
Setting objectives and defining the scope of your program.
- Developing a roadmap outlining necessary actions, timelines and resources.
- Prioritising sections based on results of risk assessments and your goals.
- Creating/ updating policies and procedures.
Operationalising and Monitoring:
Here we will focus on integrating the NIST CSF into your daily operations:
- Implementing the recommendations.
- Providing training programs to ensure staff understand their roles.
- Establishing continuous monitoring mechanisms to track performance.
- Conducting regular audits and developing an incident response plan to ensure compliance.
Evaluating and Improving:
Continuous improvement is essential for effective cyber security. Here we will evaluate the effectiveness of the controls and identify opportunities for enhancement:
- Conducting periodic reviews to measure effectiveness of controls.
- Keeping up to date with and adapting around the latest cyber security trends and regulatory changes.
- Implementing corrective measures to address any identified issues.
- Engaging in regular management reviews of the program as a whole.

Book a consultation
Book a consultation with one of our experts to understand how our VRM services can help your business…
Book a Consultation
Key Benefits of the NIST Cybersecurity Framework:
A NIST Cybersecurity framework will provide a range of benefits to your business:
Cybersecurity Management: – Improve your organisation’s protection against cyber threats and improve your security.
Compliance: – Display your commitment to best practice and complying to industry standards.
Risk Management: – Identify, assess and manage your cybersecurity risks more effectively than ever before.
Reputation: – Improve your relationships with key stakeholders and increase their trust in you and strengthen your brand.
Operational Resilience: – Reduce the likelihood of cyber security related incidents and ensure you are able to quickly recover and maintain your operations in the future.

Let’s get the ball rolling…
Get in contact with our experts to find out how our experts can help you prepare for certification.
Why You Should Choose Mondas:


Flexible Resource
Our consultants will work to meet your needs as and when they come, regardless of their complexity. Our service offers capabilities across all compliance domains; from internal assistance which aids a resource gap, to formal GAP assessments and project plans, we will be here to help. Whether it’s a short or long term engagement, we will be able to step in and drive the process for you, saving you the time and money it takes to hire your own internal team.


Skilled Staff
Our compliance services utilise only the most highly experienced and accredited consultants to step in and assist your business in preparing for certification. We will ensure that the individual we assign to your team is well equipped to manage your specific needs, meaning you can be confident in our ability to successfully support your certification process.


Specialist Support:
Our GRC team has a rich wealth of experience working as consultants for a wide range of organisations across a huge variety of industries. This means that they are highly attuned to the different challenges and obstacles which are currently facing businesses like yours. Accordingly, you can be confident in their ability to offer relevant and informed support throughout your certification process.


Cost Effective
Mondas is committed to providing advanced cybersecurity solutions at price points that work for all businesses. This means we will tailor our compliance services to align with your budgetary constraints without compromising; we provide protection using expert consultants and leading technology in every engagement.


Tailored Solutions
Our services are fully adapted to the needs of each client. Each business boasts an entirely unique portfolio of factors which must be considered when creating an effective ISMS. This means it is crucial for our consultants to offer tailored advice to support the creation of a compliant system. We will assign a dedicated consultant to your business, which will ensure that the individual you work alongside has a comprehensive understanding of your business and its compliance requirements.

Like what you’re hearing?
Speak to an expert today on 01252 494 020 or…Email UsVisit Our LinkedIn
SPEAK TO US