Zero Trust may be one of the most overused terms in recent history but do you really know what it entails? Let’s dig into the concept which is at the top of everyone’s roadmap at the moment.
What is Zero Trust?
To answer this question, we first need to look at traditional network environments. These have typically been focused on building a wall around the business with firewalls and email/web security to protect against incursions while adding some form of virus protection at the endpoint layer, this implies that everything within this walled environment is trusted. It is important to know that nearly all attack methods in the previous 5+ years have evolved to bypass these boundary protections and quietly attack organisations from the inside.
This brings us on to Zero Trust. This model simply means that all trust is removed from the environment. In this model, trust is only granted to verified entities (human and system identities), no access to assets/resources is allowed without this (and ongoing) verification and might only be granted for a limited period of time and certainly with the least possible privilege.
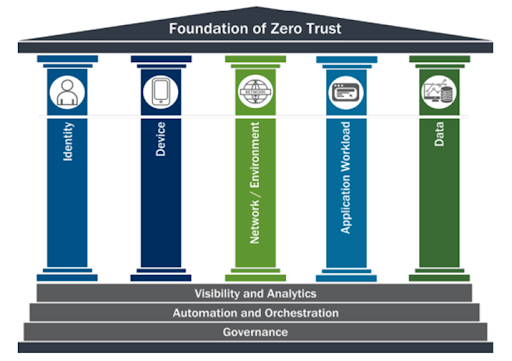
Source: CISA Zero Trust Maturity Model
Adopting this model will require that an organisation has complete control of identities, network and cloud environments, data classification, endpoint devices and the application layer. Each of these pillars are then wrapped in additional layers of logging, automation and governance. (We’ll look into these pillars and layers in our next few blogs).
Why is Zero Trust so important?
Consider the original model of information cyber security mentioned above. You’ve implemented protections at the perimeter to prevent inbound attacks but if an advanced attack as is the case with most current attacks, is successful then everything in your business is accessible and can be extracted or encrypted.

Removing all implicit trust instantly reduces your attack surface. If an attacker cannot prove that the identity they are utilising is valid and access to an asset is restricted to validated and verified accounts then the attack cannot continue. If you can implement this level of control across every layer of your environment and ensure that it works flawlessly, immediately and drastically improves your security posture.
Couple this with the improvement in cloud governance and an increased support for compliance and the choice becomes obvious.
Another reason why you might consider developing a Zero Trust roadmap is related to a possible but expected change to future governmental regulations particularly if you deal with public institutions. During 2021, the Biden administration issued an executive order requiring organisations to strengthen their cyber security defences with a focus on Zero Trust. While the UK parliament has not yet made this decision it could be expected that it will happen at some point and that any business delivering services or solutions to government bodies will be required to demonstrate their alignment to a Zero Trust framework. Just how this might be proven is not clear but one possibility is that it could be incorporated into the Cyber Essentials+ program.
Where to start?
First, understand that Zero Trust is not a single product or service. Secondly it will have an impact on the entire business.
Now consider that Zero Trust is a combination of technologies, processes and activities that must deliver automated identity management, technical access control, data protection and visibility. Lastly, you should realise that achieving Zero Trust is not a short term project.
Now consider the following questions:
- What are you trying to protect?
- What threats are you protecting it from?
You will have to detail these, including an accurate register of your assets and entities. From this develop an achievable and measurable roadmap and project plan based on your findings. Next step will be to “sell” the plan to your executive team. Ideally you should identify someone in this group who would be willing to be the program sponsor for the project and support your plan and efforts across the business.
In the previous section, it is worth noting the three critical terms “valid, verified and restricted”. Having complete control over your identities is where organisations should initially focus their efforts. Controlling the entire lifecycle of human and system identities from creation (onboarding) to termination (deletion) is crucial to implementing Zero Trust. Some might say “ that sounds easy, we’ll use our active directory to do that”, but this level of control over your identities requires new solutions, processes and a significant amount of automation.
This is where the newer generation of identity and access management comes into play. Without mentioning specific products, the required IAM solution or service you choose must integrate with your human resources system/s, your existing identity store/s, all applications, SIEM platform, MFA services, cloud platforms and every network security gateway (firewalls, email and web gateways).
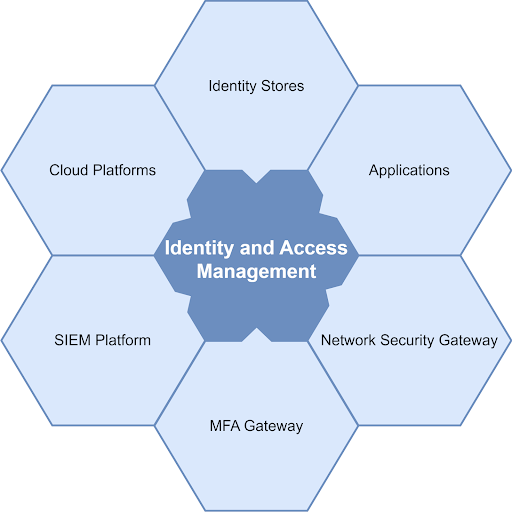
It should automate all simple tasks to reduce administrative burdens on your support teams by orchestrating identity creations, transfers and terminations while applying or removing permission sets when role changes occur.
Now that we’ve very briefly mentioned network controls, this is another area that is crucial to protecting access to resources located across your networks. Ideally all of these technologies should support identity based access. Segregate the network based on the criticality of the assets in each segment and limit any access to these to trusted and necessary applications and identities. Separate confidential and public applications and databases and place each in different network segments with the relevant access control policies.
A parallel workstream should be started to integrate all remote access services with the IAM platform to authenticate the user and device requesting access, profile the session requirements, force the use of multifactor authentication and apply any policy and posture requirements before allowing access. Remember to include Zero Trust compatibility, specific to your existing solutions or services when deciding on any future controls.
For obvious reasons, if you do not have visibility of events in your Zero Trust technology then you cannot effectively act on or apply the automation required to manage it appropriately.
The next step should be the effective collection of logs from all components of your identity, security, network and application stack. Preferably these logs should be made available to your management and SOC layers in real time to enable fast decision making and reduce response times.
In general, the architecture principles that your approach to Zero trust should adhere to are:

In our next few articles on this subject we will delve into each pillar in more detail to understand the areas of focus for each and how each fits into the larger enterprise security program.
To conclude this high level introduction to Zero Trust it is worthwhile reiterating some of the points above. Starting on this path requires executive support and budgetary investment in your plan and completion will not be achieved in a year. There are some initiatives that can quickly reduce your risk posture such as implementing multi factor authentication, strictly enforcing remote access and strengthening your identity control but in general you will be required to modify operational processes, replace or refresh technical controls and effectively manage these changes to your organisation.
Got a question? Get in touch to speak to one of our specialist consultants about Zero Trust today!
Additional reading
NIST Zero Trust Architecture: https://www.gartner.com/doc/reprints?id=1-2982XEE0&ct=220223&st=sb
CISA Zero Trust Maturity Model: https://www.cisa.gov/sites/default/files/publications/CISA%20Zero%20Trust%20Maturity%20Model_Draft.pdf
Gartner Practical Projects for Zero Trust: https://www.gartner.com/doc/reprints?id=1-2982XEE0&ct=220223&st=sb
Zero Trust – Where is the UK: https://tbtech.co/blockchain/security-and-data/in-a-zero-trust-world-where-is-the-uk/