
Introduction
At MONDAS, we are dedicated to prioritising cybersecurity for your company. We understand the critical role that security plays in safeguarding your digital assets, sensitive information, and overall business operations. That’s why today we want to talk about pen testing and its implications for cybersecurity. By delving into the world of pen testing and highlighting the best practices and tools, we aim to equip your company with the knowledge needed to enhance its security defences. With MONDAS, you can count on our expertise, cutting-edge solutions, and commitment to helping you navigate the ever-changing cybersecurity landscape. Trust us to guide your company towards a robust security posture and enable you to face cyber threats with confidence.
What is pentesting?
Pen testing, also known as penetration testing or ethical hacking, is the practice of testing computer systems, networks, or applications to identify vulnerabilities that could be exploited by attackers. Pen testing plays a crucial role in proactively assessing the effectiveness of security controls, validating the resilience of the system, and improving overall cybersecurity readiness.
What can it be used for?
A penetration test is performed by security professionals who attempt to exploit weaknesses in an organisation’s defences, using the same techniques and tools that a real attacker might use. The aim is to identify security flaws that could be exploited by malicious actors, and to provide recommendations for improving the security posture of the organisation.
The ultimate goal of a penetration test is to improve the security of an organisation’s systems and data by identifying vulnerabilities before they can be exploited by attackers. By doing so, organisations can reduce the risk of cyber attacks, protect their sensitive data, and maintain the trust of their customers and stakeholders.
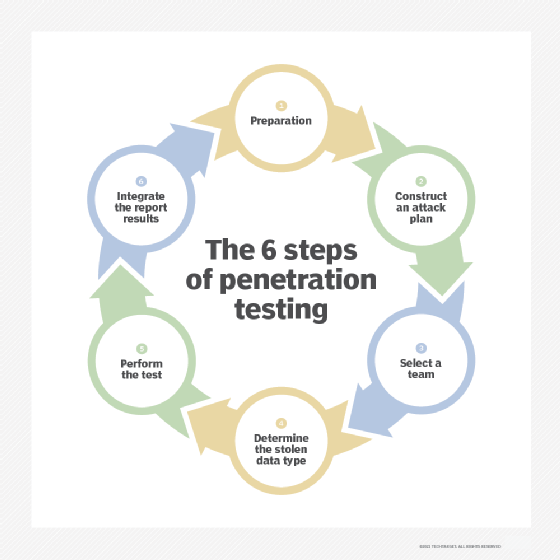
How to do pentesting?
A proper penetration test involves a systematic approach to assess the security vulnerabilities of a system or network. The process typically consists of several stages. First, the reconnaissance phase involves gathering information about the target system, such as IP addresses and domain names, to understand its architecture and potential entry points. Next, the scanning stage involves using various tools to identify open ports, services, and potential weaknesses. Once vulnerabilities are identified, the exploitation stage begins, where testers attempt to exploit the vulnerabilities to gain unauthorised access or control. This stage aims to simulate real-world attacks and assess the system’s resilience. Following the exploitation, testers document their findings and present them to the organisation, highlighting the risks and suggesting mitigation strategies. Finally, the remediation stage involves addressing the identified vulnerabilities and implementing security measures to strengthen the system’s defences.
What are some of the most commonly used tools in pentesting?
There are a lot of different tools out there, but here we list some of the most popular and effective tools used in pen testing. These tools have been widely adopted and trusted by security professionals due to their robust features, versatility, and proven track record in identifying vulnerabilities and strengthening cybersecurity defences. By leveraging these popular and effective tools, security professionals can uncover weaknesses, remediate vulnerabilities, and bolster overall security resilience in the face of evolving cyber threats.
Nmap
Nmap, short for “Network Mapper,” is a versatile and widely used open-source network scanning tool. It is designed to discover and map networks, identify open ports, and gather information about networked devices. Nmap allows users to conduct comprehensive scans to assess the security and availability of networked systems. It employs a variety of scanning techniques, including TCP, UDP, and ICMP scans, to probe target hosts and determine their status and services. Nmap’s flexible scripting engine enables users to create custom scripts for specialised scanning and automation purposes. With its extensive range of features and options, Nmap provides valuable insights into network topologies, potential vulnerabilities, and the overall security posture of a network. It is an essential tool for both security professionals and network administrators, assisting in network exploration, vulnerability assessments, and ensuring robust network defences. Nmap can also be used to identify hosts that are connected to the network and map out their topology.
Metasploit
Metasploit is a powerful and widely utilised penetration testing framework that enables security professionals to simulate real-world attacks and assess the vulnerabilities of target systems. It provides a comprehensive suite of tools, exploits, and payloads to test and exploit known vulnerabilities. Metasploit allows users to conduct various penetration testing activities, such as reconnaissance, scanning, and exploitation. Its extensive database of exploits and payloads can be leveraged to identify and exploit security weaknesses in systems, applications, and networks. Metasploit also offers post-exploitation modules to gain further access and control over compromised systems. Its flexible and modular architecture allows users to customise and automate their penetration testing processes. However, it is important to emphasize that Metasploit should be used responsibly and ethically, with proper authorisation and consent. With its robust capabilities, Metasploit remains a popular tool for security professionals in identifying and addressing vulnerabilities, thereby strengthening the overall security posture of organizations.
Wireshark
Wireshark is a widely used open-source network protocol analyser that allows users to capture and analyse network traffic in real-time. With its rich feature set and intuitive interface, Wireshark provides deep insights into network communications and helps diagnose network issues, detect security threats, and troubleshoot problems. By capturing and dissecting packets, Wireshark allows users to examine protocols, view packet details, and analyse network behaviour. It supports a wide range of protocols and provides advanced filtering and searching capabilities, making it a versatile tool for network analysis. Wireshark is commonly used by network administrators, security professionals, and developers to understand network performance, identify anomalies, and investigate security incidents. Its ability to capture and analyse network traffic in a user-friendly manner makes Wireshark an invaluable resource for maintaining network integrity, optimising performance, and ensuring the security of networked systems.
John the Ripper
John the Ripper is a popular and powerful password cracking tool used by security professionals and system administrators to assess the strength of passwords and identify potential security vulnerabilities. It is capable of performing both offline and online password cracking by utilising various techniques such as brute force, dictionary attacks, and rainbow table attacks. John the Ripper supports a wide range of encryption algorithms and can handle password hashes from various operating systems and applications. Its flexibility and customisable nature allow users to fine-tune the cracking process and adapt it to their specific needs. By running password cracking tests with John the Ripper, security experts can evaluate the effectiveness of password policies, identify weak passwords, and improve overall security by enforcing stronger password requirements. However, it is important to note that John the Ripper should only be used on systems and accounts with proper authorisation to ensure ethical and responsible use.
Aircrack-ng
Aircrack-ng is a powerful and widely used open-source tool for assessing and cracking wireless network security. It focuses on the security of Wi-Fi networks and is primarily utilised by security professionals and penetration testers to identify vulnerabilities and strengthen wireless network defences. Aircrack-ng combines several tools into a comprehensive suite, including packet sniffing and capturing, network monitoring, and password cracking. By capturing and analysing network traffic, Aircrack-ng can attempt to crack WEP and WPA/WPA2-PSK keys using various attack methods like brute-force, dictionary, and statistical attacks. It provides robust features for monitoring and analysing Wi-Fi networks, allowing users to identify insecure network configurations, detect unauthorised access, and assess the strength of encryption protocols. It’s worth noting that Aircrack-ng should only be used ethically and with proper authorisation on networks that you have permission to assess. With its powerful capabilities, Aircrack-ng is an invaluable tool for evaluating and improving wireless network security.
Burp Suite
Burp Suite is a comprehensive web application security testing tool widely used by security professionals to assess the security posture of web applications. It offers a range of powerful features that help identify and exploit vulnerabilities. Burp Suite acts as a proxy, allowing users to intercept and modify web traffic, analyse requests and responses, and perform detailed manual testing. It includes a powerful web scanner that automates the identification of common security issues, such as cross-site scripting (XSS) and SQL injection. Burp Suite also provides a robust suite of tools for advanced testing, including session handling, automated crawling, and targeted attacks. Its extensibility through plugins allows users to customise their testing workflow and add additional functionality. Burp Suite is a versatile tool that helps security professionals evaluate the security of web applications, identify vulnerabilities, and provide recommendations for remediation. With its comprehensive set of features, Burp Suite is an essential tool for any security testing arsenal.
Hydra
Hydra is a powerful open-source password cracking tool widely used for brute-force and dictionary attacks against various protocols and services. It is designed to test the strength of passwords by systematically attempting different combinations until the correct one is found. Hydra supports a vast range of protocols, including FTP, SSH, Telnet, HTTP, and more. It can be used to assess the security of network services by attempting to crack weak or easily guessable passwords. Hydra’s versatility allows for customisation of attack parameters, including the choice of dictionaries, character sets, and threading options. However, it is important to emphasize that Hydra should only be used on systems and accounts with proper authorization and consent. As a tool in the hands of security professionals and penetration testers, Hydra can aid in identifying weak passwords, reinforcing the importance of strong authentication practices, and highlighting the need for robust password policies and practices.
FOCA
FOCA (Fingerprinting Organisations with Collected Archives) is a powerful information gathering and metadata analysis tool designed to extract valuable information from various file formats, including documents, PDFs, and websites. It aids in the reconnaissance phase of security assessments and is widely used by penetration testers and security professionals. FOCA automatically scans documents and extracts metadata, such as author names, email addresses, network information, and hidden data, to build a comprehensive profile of the target organisation. It also analyses the structure and content of websites to identify potential vulnerabilities or information leakage. FOCA provides a user-friendly interface and generates detailed reports, helping users understand their organisation’s online footprint and potential security risks. With FOCA, security professionals can gather valuable intelligence to assess the security posture of an organisation, identify potential attack vectors, and implement necessary security measures to protect against potential threats.
SQLMAP
SQLMap is a widely recognised open-source penetration testing tool used to detect and exploit SQL injection vulnerabilities in web applications that interact with databases. It automates the process of identifying and exploiting SQL injection flaws, making it an essential tool for security professionals and ethical hackers. SQLMap supports a variety of database management systems and provides a comprehensive range of features, including automatic detection of vulnerabilities, fingerprinting of database systems, dumping data from databases, and executing custom SQL queries. It offers advanced techniques like time-based blind SQL injection and error-based SQL injection to extract valuable information from databases. With its user-friendly command-line interface and extensive capabilities, SQLMap simplifies the process of identifying and exploiting SQL injection vulnerabilities, thereby enabling security teams to proactively secure web applications and prevent potential data breaches. However, it is important to note that SQLMap should be used responsibly and ethically with proper authorisation to avoid any unauthorised access or misuse.
NIKTO
Nikto is a popular open-source web server scanning tool used by cybersecurity professionals and penetration testers to assess the security of web servers. Its primary purpose is to identify potential vulnerabilities and misconfigurations that could be exploited by attackers. Nikto performs comprehensive scans against target web servers, examining for common issues such as outdated software versions, server misconfigurations, and known security weaknesses. It analyses various aspects, including server headers, SSL/TLS vulnerabilities, outdated software, and insecure files or directories. Nikto provides detailed reports of identified issues, allowing security teams to address them promptly. With its user-friendly interface and extensive database of known vulnerabilities, Nikto is a valuable asset in any web security arsenal, helping organisations identify and remediate web server vulnerabilities before they can be exploited.
OWASP ZAP
OWASP ZAP (Zed Attack Proxy) is a powerful and widely used open-source web application security scanner and penetration testing tool. Developed by the Open Web Application Security Project (OWASP), ZAP is designed to help identify vulnerabilities and security weaknesses in web applications. It operates as a proxy server, intercepting and analysing web traffic to identify potential vulnerabilities such as cross-site scripting (XSS), SQL injection, and insecure direct object references. ZAP provides a user-friendly interface that allows security professionals to manually explore and test web applications, as well as automated scanning capabilities for comprehensive vulnerability assessments. It offers various features like active and passive scanning, fuzzing, and automated script execution. ZAP’s extensibility allows users to create custom scripts and plugins to enhance its functionality. With its extensive set of features, OWASP ZAP is a valuable tool for assessing and enhancing the security of web applications, helping organisations proactively identify and address vulnerabilities before they can be exploited.
NESSUS
Nessus is a widely recognized and powerful vulnerability scanning tool used by cybersecurity professionals to identify and assess security vulnerabilities in networks, systems, and applications. It provides comprehensive vulnerability scanning capabilities, allowing users to scan their assets for known vulnerabilities, misconfigurations, and weaknesses. Nessus leverages a vast and regularly updated vulnerability database to identify potential risks, including software vulnerabilities, insecure configurations, weak passwords, and more. It offers both active and passive scanning methods, enabling users to perform network-based or host-based assessments. With its intuitive interface and customisable scanning options, Nessus allows users to prioritise and address vulnerabilities based on severity levels. It generates detailed reports that provide actionable insights, helping organisations strengthen their security posture and prioritise remediation efforts. Nessus is a valuable asset in any organisation’s cybersecurity toolkit, facilitating proactive vulnerability management and reducing the risk of potential attacks.
Conclusion
By conducting regular penetration tests, your company can proactively identify vulnerabilities, weaknesses, and potential entry points that malicious actors may exploit. It allows you to gain an in-depth understanding of your security posture and assess the effectiveness of your existing defenses. Penetration testing not only helps you detect and mitigate potential risks but also enables you to strengthen your overall cybersecurity resilience. By investing in penetration testing, you demonstrate your commitment to protecting your sensitive data, maintaining customer trust, and safeguarding your company’s reputation. With the insights gained from penetration testing, you can make informed decisions, implement targeted security measures, and stay one step ahead of cyber threats. Ultimately, caring about penetration testing is a crucial step towards ensuring the long-term security and success of your company.
If your organisation needs any help with penetration testing, our experts are ready to help! All you need to do is get in touch.





